Always nice to be solicited for a role you’d like. That hasn’t happened to me often but recently I got a call about a position. That was followed up with an email. Then another call. Then a few emails and calls with the first caller’s senior recruiter. All in the space of three hours or so. Everything was rolling along and… crickets after my last email. Was it me?
I don’t think so, but you be the judge.
The position I was solicited for was IT Manager. One requirement that I didn’t have was SCRUM Master certification. But, so long as the certificate was earned within six months of start date that would be acceptable. It’s not common, but I have seen positions that require a certification and will accept it being earned within a certain period after starting.
I tell the people I’m speaking with on the phone I need a little time to investigate the certification and see if it seems like something I can achieve in six months. They say fine, they’ll call back in an hour or so and see if I’m still interested.
At this point I’ve gotten the consulting company’s name, the organization they’re recruiting for, and time frame when the position is to be filled.
After a bit of web searching I find a number of training organizations offering online SCRUM Master Certification training at a range of prices. It’s affordable from my point of view so I’m thinking… commit. I really am looking for a new opportunity.
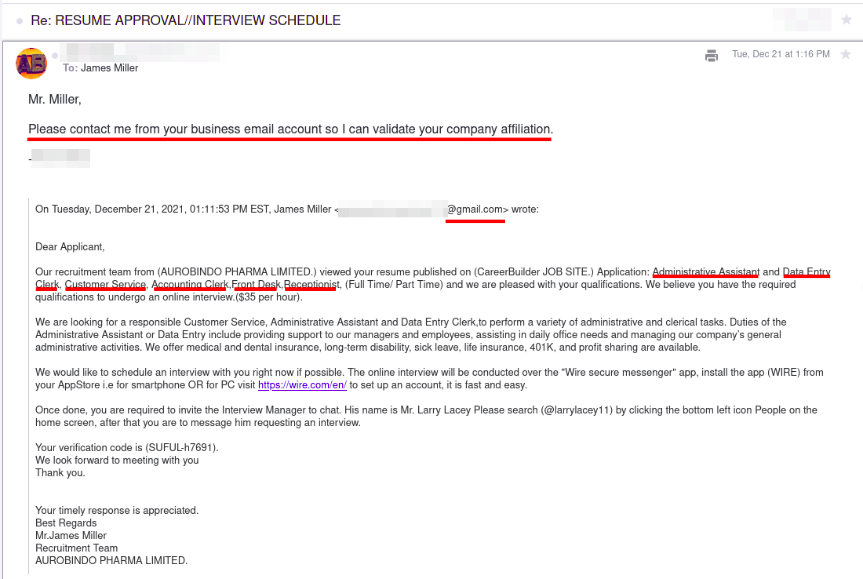
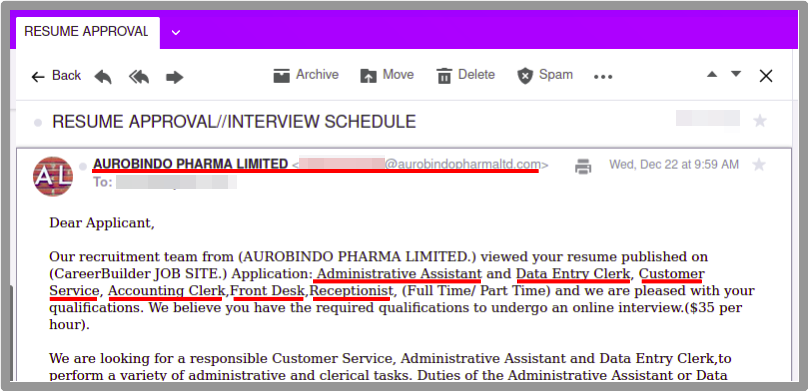
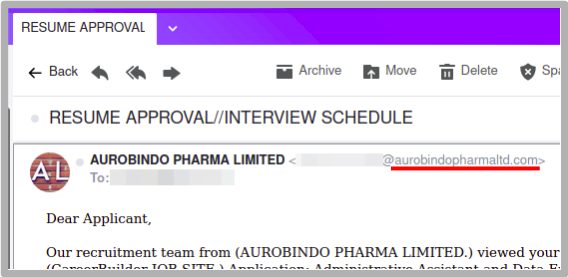
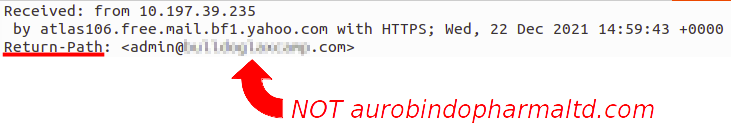
I also check out the recruiter’s domain to find out how long its been around. Surprise, surprise, it’s only a few months old. Red Flag #1. Then I check website of the customer they’re recruiting for to search for the position. The position isn’t listed. Red Flag #2.
Finally they call back and we talk about the position. I tell them I’ve found a trainer that looks like they have a good online training program set up and the course is affordable. As soon as I tell them the trainer I’m told, “no, that’s not such a good trainer.” Red Flag #3. I’m given another training company’s name and told I should register right away so we can provide proof to the employer I’m taking steps to have the certification by the deadline. “Right away”, Red Flag #4.
I tell them to give me a few moments to check out that trainer’s website. Wouldn’t you know, the trainer’s website is even newer than the recruiters. Red Flag #5.
At this point I really don’t believe this is legit and ask for a contact at the company they’re recruiting for to confirm with them the position is open and the certification requirement.
End of conversation. Sigh. It was nice to be recruited for a position I am well qualified for and points to the sophistication of the scam. It was tailored to my skills. Disappointing that it was only a scam to get my money for a certification training course that likely wouldn’t have provided any training.
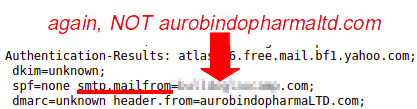
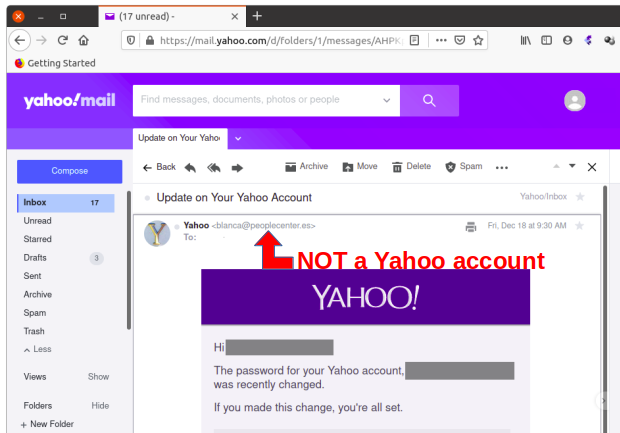
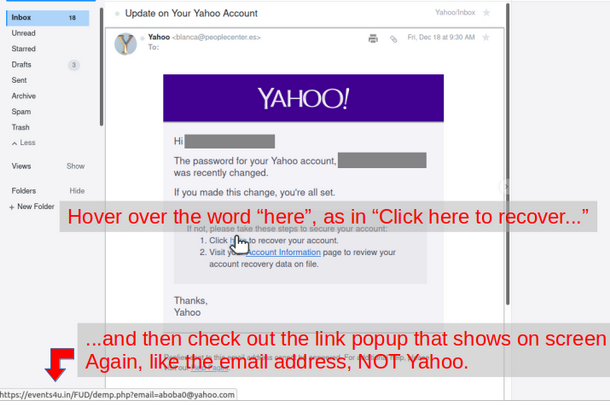
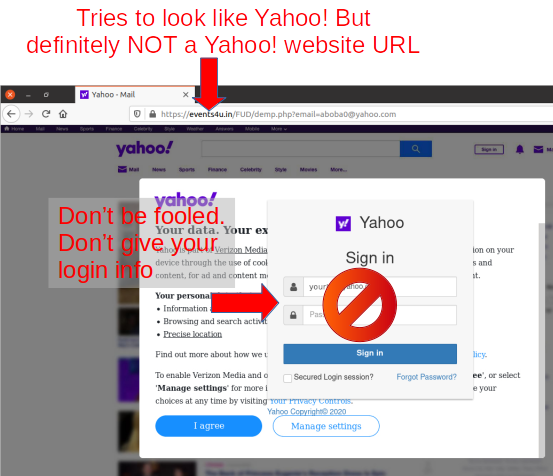
This all happened several months ago. At this point the “recruiter’s” website is still up. Doesn’t look changed much. All boiler plate stuff. The training company’s website isn’t accessible. Clearly, be suspicious, ask questions and investigate the answers to keep yourself from being taken.