I am unemployed due to COVID-19. Probably something that’s happened to many of you. I’ve also been searching for work continuously, continuously, since loosing my director of IT role. I have not gotten an offer on anything equivalent and have had periods of unemployment where I didn’t get responses for anything I applied to. The low point was when I was so desperate I applied for an hourly position at Dunkin Donuts and they didn’t call me back! I have gotten help desk roles and that position is what recently ended due to coronavirus.
Since I have been continuously searching for employment for years I’ve got accounts on all the major job boards, CareerBuilder, Monster, Beyond, Indeed, and many minor and regional ones too. And of course I use LinkedIn. My profile is here, Alan Boba. Message me if you need someone to manage your technology.
Recently I was very disappointed by the response I got back from an application, “Thank you but we’re not interested in you”. The position was very local to me which would have been great. And the IT Manager job description was one I would have written if asked to write one that was an exact match for my skills. I was really hopeful when I sent the application and very very disappointed when the rejection came. Not even a phone screen.
Next position I applied for on CareerBuilder I was presented with a message as soon as I completed the application, “would you like to instantly apply to these 26 matching jobs?” Typically I review job title and description, check the location and do some other review before applying for a position. This time I just hit “apply”. Right away CareerBuilder came back with a similar “instant apply” message and again I clicked “apply”. This kept happening. I kept clicking. I figured to be clicking until “matching jobs” ran out. They never did. I stopped clicking after instant applying to about 500 or so “matching jobs”.
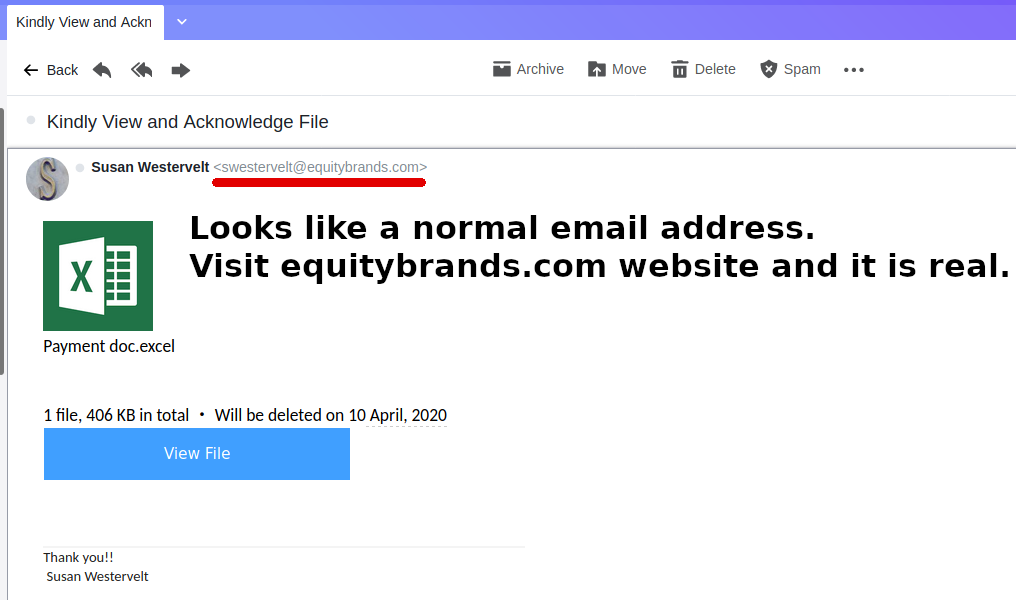
Wouldn’t you know… next day I was getting invitations to online interviews. I was skeptical and cautious. The biggest and most immediate red flag was that all the “interviews” were with people using @aol.com and @gmail.com email addresses. No business emails. But hey, I didn’t have any real offers to reply to and who knows, maybe I’m just too suspicious and one of these was real.
One of them even said they were part of an agribusiness that was started in Australia and expanding in USA. The business is real and it even has two locations in the western US that were correctly identified in the chats.
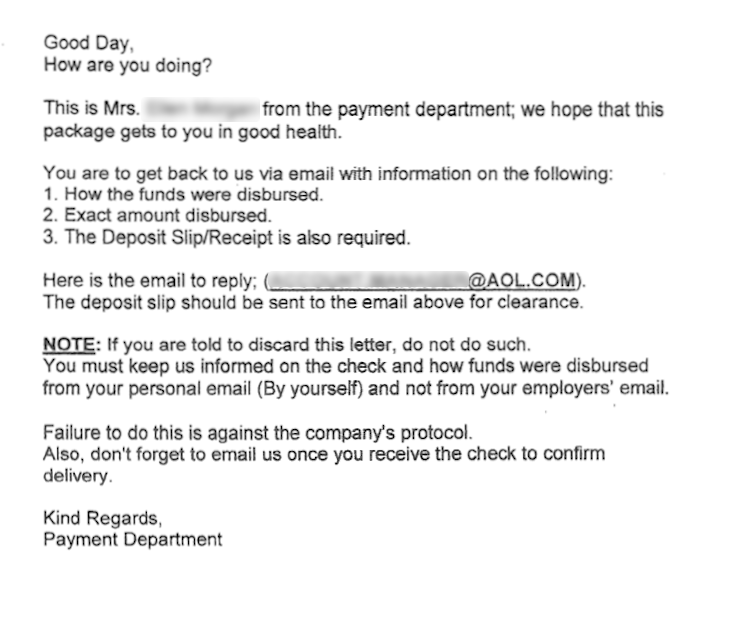
I received a check by FedEx, almost $4,000! Ostensibly to buy equipment I would need for my office. A cashiers check though, not a check drawn from a business account. The letter that came with it is on plain paper, not office stationery. It doesn’t say what I should buy and doesn’t have a business name or address. Plus I am again directed to communicate with a non-business email account, @aol.com.
I’ve tried to validate the check’s bank routing number and two of the three routing number websites I’ve found recognize the routing number. I’ve also scanned the check front and back. No watermarks show up in either scan. And the check doesn’t have a stamp on it’s face with “valid for xxx days”. A stamp I’ve seen on every cashier’s and corporate check I ever recall handling.
For now I’m still thinking this is a scam. But I’ll play along because I’ve got the time and I’m unemployed. And who knows, maybe I am just too suspicious.
In case you’re curious and want to see what I’ve received so far, take a look at the letter and check that came in the FedEx package. It does cost money to send via FedEx. So unless a business’ FedEx account has been hijacked the scammers have spent some money to send me the check.