Switched recently to OpenSUSE Leap on my backup laptop. Then found the simplest solution for me to sync Google Drive with OpenSUSE was to change to OpenSUSE Tumbleweed. Great. Done. Now time to get Tumbleweed to be a remote client to my Debian primary laptop.
For years, the primary laptop has run Ubuntu. Recently switched it to Debian 12 bookworm for the reasons documented here, From Ubuntu/Zorin to Debian/OpenSUSE. The remote solution to connect to the primary laptop has been RealVNC.
Debian 12 bookworm is using Wayland, and the latest Ubuntu is using it too. RealVNC isn’t compatible with Wayland so isn’t compatible with the latest Ubuntu or Debian. For myself, remote control hasn’t been a need for a few years so I didn’t realize RealVNC wasn’t Wayland compatible. As soon as I wanted remote control again, Wayland compatibility became an issue.
Do a little digging and find NOMACHINE works with Wayland. Install NOMACHINE on the Debian primary laptop, client and server running, no problems.
Install on the OpenSUSE Tumbleweed laptop, install fails. Server service isn’t found and client won’t start. 🫤
Check out NOMACHINE compatibility, it includes OpenSUSE 15.x. Leap is 15.x, current Tumbleweed is 20250714. Tumbleweed is on the backup laptop to make Google Drive work. I NEED Google Drive syncing between the primary and backup laptop. Can I get NOMACHINE working on Tumbleweed?
First, let’s see what NOMACHINE looks like when it’s running. Spin up an OpenSUSE Leap 15.x virtual machine and install NOMACHINE. It works fine, can connect to Wayland displays from X11 virtual machine. Now to troubleshoot the installation on OpenSUSE Tumbleweed.
Spin up a Tumbleweed virtual machine and do a NOMACHINE installation. (virtual machines are indispensable and readily available troubleshooting and simulation tools)
Terminal output during installation on Tumbleweed is brief and indicates nxserver.service can’t be loaded.
Check the installation log, /usr/NX/var/log/install.log, find an error earlier than nxserver.service . The error, “execstack can't be run.” Check what is exestack and find execstack isn’t installed. Install it and run NOMACHINE installation again. Terminal output remains the same and nxserver.service can’t be loaded.
Back to the log and find a message, Warning: SELinux userspace will refer to the module from /usr/NX/scripts/selinux/nx-unconfined.pp as nx rather than nx-unconfined. Since nxserver.service won’t run and there’s a Warning that SELinux has a problem with something NX related I turn to finding out how to understand the SELinux problem.
Aside from knowing SELinux enforces access control policies on OpenSUSE Linux, I haven’t been aware of it before. Digging around to get an idea of what the warning means I find a tool called SELinux Troubleshooter. It’s in Tumbleweed’s Discovery app library, so I install it.
So, now, the execstack problem has been handled and a way to diagnose the possible SELinux issue installed. Time to run the NOMACHINE installation again.
Bingo!
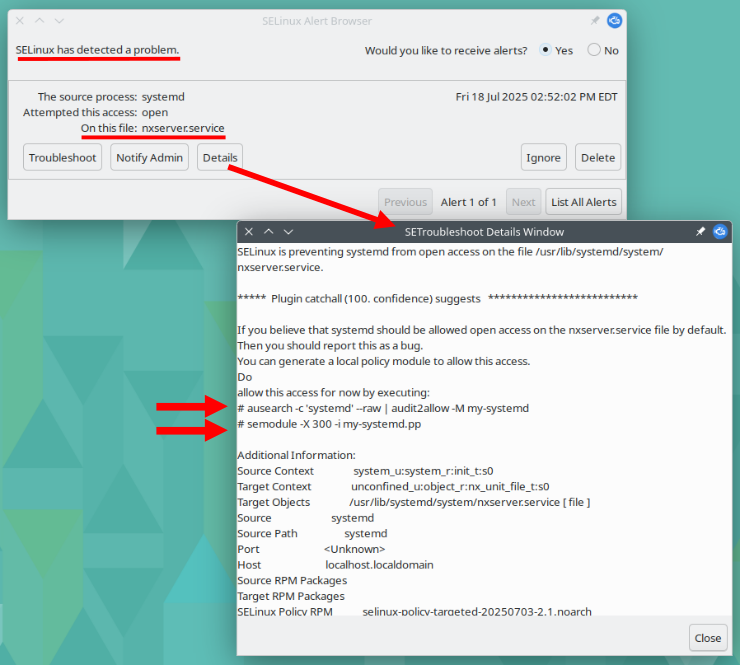
The Troubleshooter provides two SELinux command recommendations. I apply the commands and NOMACHINE is now running on OpenSUSE Tumbleweed just fine. (At least on Tumbleweed 20250714.)
I still like RealVNC’s interface and modes of operation better. I’ll continue to watch it for Wayland compatible releases and continue to upgrade NOMACHINE with new releases, especially if they include better access to controls, something like a pop up tool bar attached to the host’s window border.
The “page peel,” NOMACHINE’s toolbar, isn’t always available depending on the Display option selected. Knowing the keyboard option, Ctrl+Alt+0, to call the NOMACHINE control center before selecting a display option that can’t display the “page peel” is a real panic avoidance tip.
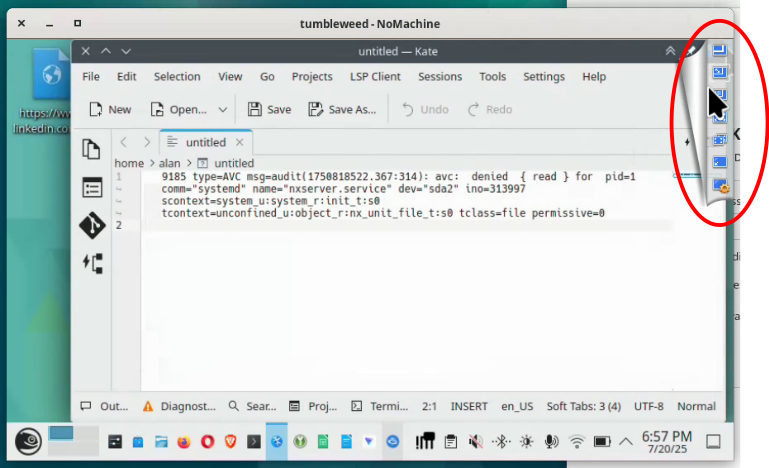
The Ctrl+Alt+0 shortcut displays the NOMACHINE control center that fills the entire client window.
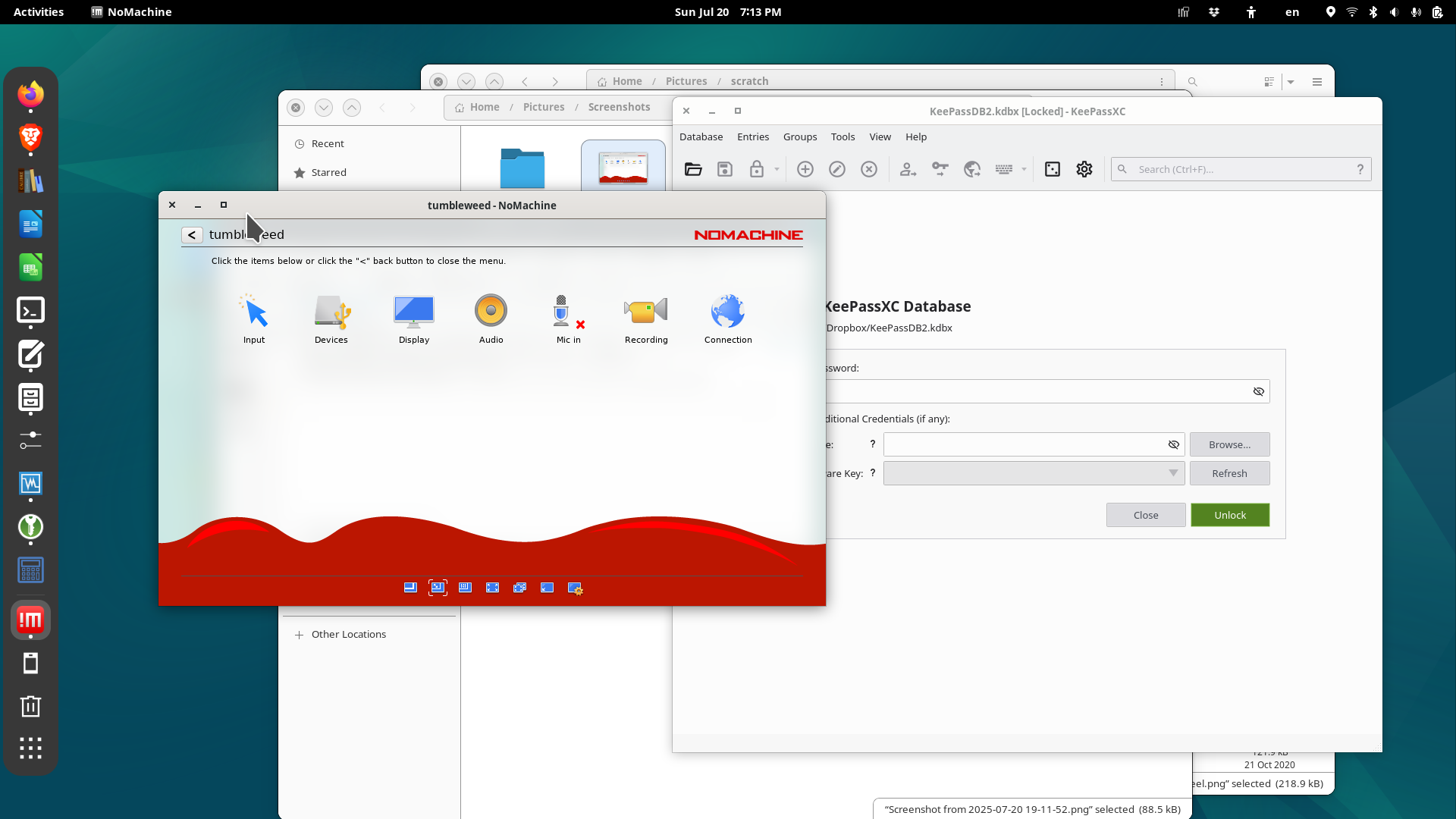
With the control center filling the entire client window the mouse can move outside the client window and interact with other applications on the client pc. In the control center, navigating the menu requires clicking an icon to reveal the icons in the next sub menu and click again and again until the target operation is reached.
Once the operation is completed each menu must be clicked to return to the menu above until reaching the top menu, the control center, and finally close the control center to display the remote control session. That’s really cumbersome navigation.
The “page peel” only has controls for the video connection and causing the “page peel” to appear doesn’t release the mouse to leave the window. The only way I’ve found to leave the NOMACHINE remote client window is to use Ctrl+Alt+0 to bring up the NOMACHINE window overlay/control center, at that point the mouse can leave the window boundaries.
If the machine hosting the NOMACHINE server has multiple monitors an option to display all monitors can be selected. However all remote monitors are squished into a single NOMACHINE client window instead of having one window for each monitor. Not very useful.
If the client and server BOTH have two monitors the “Fullscreen on all monitors” option can be selected. In this configuration one each of the remote system’s monitors fills one each of the client system’s monitors. This feels very much like sitting at the remote system as opposed to controlling it remotely. However, again, there is no way to leave the remote control session’s window and interact with the client system without first displaying the top level NOMACHINE window to then be able to navigate around the client computer.